Cisco Umbrella Threat intelligence is End-of-Life
When you analyze over 620 billion internet requests a day, you see what other security solutions miss
End-of-Life for the Cisco Umbrella software
Software maintenance will end on April 2, 2025. No patches or maintenance releases will be provided for Umbrella Roaming Client after that date.
Application software support will not be available for the stated software versions beyond April 2, 2025.

Using threat intelligence to see cyber attacks before they launch
We see the relationships between malware, domains, and networks across the internet. Similar to how Amazon learns from shopping patterns to suggest the next purchase, our threat analysis learns from internet activity patterns to automatically identify attacker infrastructure being staged for the next threat.
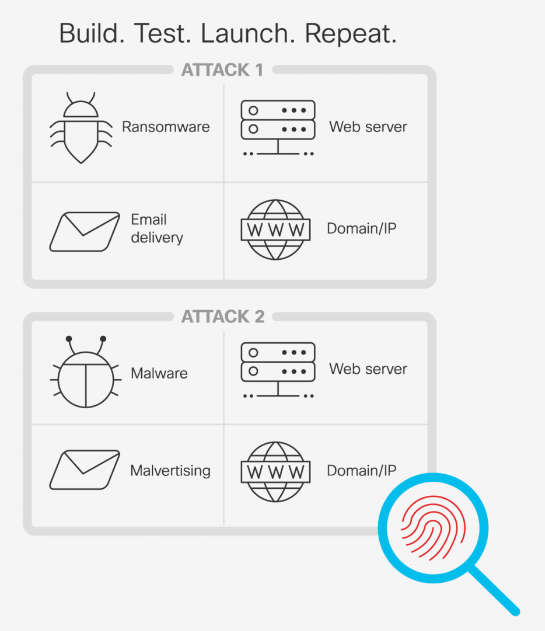
Attacks don’t just suddenly happen
The development lifecycle to create new attacks is similar to that of new applications. An app developer builds something, tests it, and then launches it. Attackers do the same, which requires infrastructure, malware, and a web or email delivery scheme. While they modify and create new malware (e.g. ransomware variants) and draft new phishing emails, attackers often reuse the exact same infrastructure (e.g. web servers and IPs) for multiple attacks — leaving behind cyber fingerprints. We focus our cyber threat analysis on identifying those fingerprints, so we can pinpoint current attacks and even uncover emerging threats being staged.
Datasets must be diverse, global, and live
Daily internet requests
Global customers
Countries worldwide
Leveraging threat intelligence from Cisco Talos, one of the largest commercial threat intelligence teams in the world, Umbrella uncovers and blocks a broad spectrum of malicious domains, URLs, and files that are being used in attacks.
Umbrella gathers 620 billion internet requests from over 24K+ customers spanning 190 countries every day at the moment a request is made. Our real-time DNS data is also enriched with diverse public and private data feeds. With such a massive and diverse data set, our threat analysis can uncover patterns that signal malicious behavior.
Making discoveries through DNS resolution
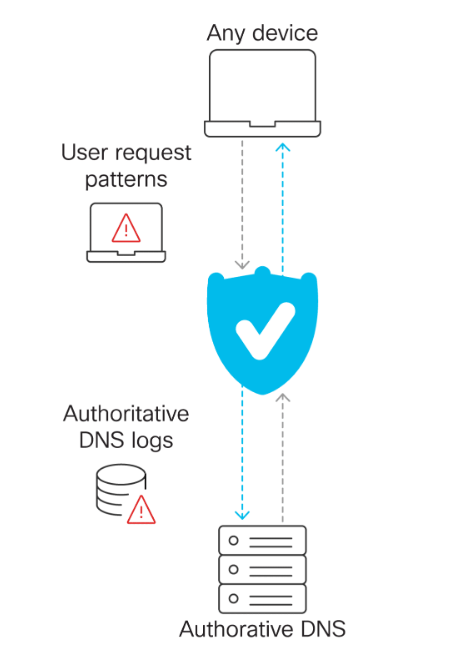
We analyze the request patterns to detect many types of threats and anomalies. For example, we can determine if a system is compromised based on the types of requests it’s making. If a device is making requests to a number of known-bad domains, it’s more likely to be compromised. The user requests patterns across our user base give us great insight into potential threats.
In the second part of the process, if our global cache doesn’t have a non-expired response to the request, then we recursively contact all of the nameservers that are authoritative for the domain requested. This process gathers authoritative logs for virtually every domain daily, which we use to find newly staged infrastructures and other types of anomalies.

A new approach to security research
There is no army of security researchers big enough to manually identify every threat. We look at things differently. The Cisco Umbrella security researchers take mathematical concepts and find new ways to apply them to security data — helping us uncover threats before attacks even launch. Our security researchers leverage advanced data mining techniques, 3D data visualization, and security domain expertise to develop the statistical models behind our threat intelligence and analysis.
Efficacy is king
Threat intelligence is one thing, but you also need to act on all of that data. Cisco Umbrella has the horsepower to actively process and enforce more than 170 million malicious DNS queries per day. And we’re constantly discovering new vulnerabilities — 200+ new vulnerabilities are found every year. Plus, Umbrella can be deployed enterprise-wide in minutes — making it one of the easiest ways to start protecting users.